
[homepage] [search]
Beware of malicious codes that may be embedded in Zip files!
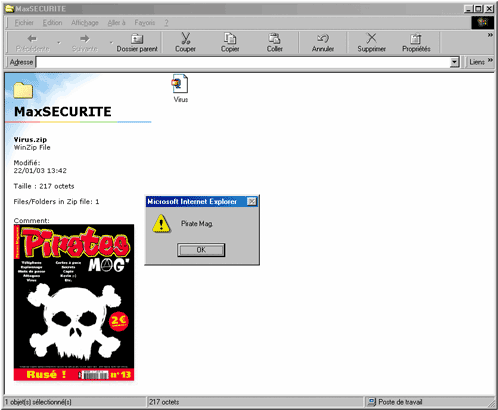
Max14H44, one of our readers, contacted us concerning a security hole he discovered in the famous compression software Winzip. In the "comments" section of a Zip file, if you add some Javascript between the [script][/script] beacons, the code will be filtered. On the other hand, if you include it inside others HTML beacons, the script will be executed when you preview the file. Demonstration. Create a Zip file containing, for example, a text file named 1.txt. Double click on this zip file. When Winzip is launched, select Comments in the Action Menu. Add the following line: [img src=' javascript:alert(' Pirate Mag ')'], then close Winzip. Under Windows 98, set the folder containing the zip file to be displayed as a "Web page" in the Tools menu, then Files Options. Click on the Zip file, the Javascript is automatically executed, displaying an Alarm Box with the inscription "Pirates Mag". We can imagine that a pirate would want to take advantage of this hole by including the "windows.open" function which would order the opening of a Web site containing a VBScript attack. Somewhat, it reminds us of the problems encountered with webmails... We contacted the authors of the Winzip software about this issue, they told us that they have been able to reproduce it and that they're working on a fix. "I am afraid that I cannot give you a specific estimate", they answered us concerning the release date of a forthcoming version.
More than three months later, the security hole is still there.
Jay
[contact & legal & cookies] © ACBM